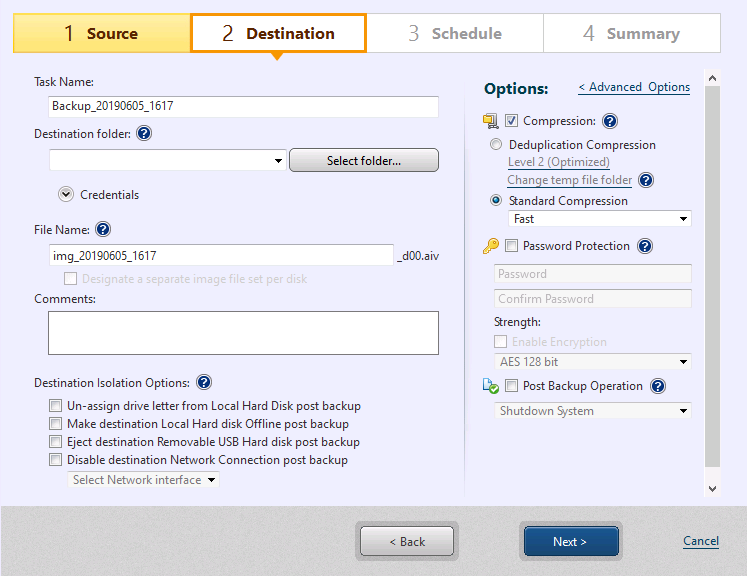
Select a destination storage for the backup image files and, specify names for both the backup image file and the backup task.
Add a brief description in the [Comments] textbox.
Destination and Option settings
Select Destination
-
Task Name: Specify the name for the backup task.
-
Destination Folder: Specify the destination folder for the backup image by entering the path and folder name or use the
 to browse to the backup destination folder.
to browse to the backup destination folder.
* Before creating a schedule by specifying a USB device for the destination, please refer here. -
File Name: The default file naming convention is applied to include the current date/time. Edit the file name as needed.
-
Comments: Use the textbox to enter a brief description of the backup image file.
-
Destination Isolation Option: Disconnects access to backup image storage drives after backups complete. Upon completion of the backup task, the specified destination storage becomes inaccessible.
* The combined use of the Destination Isolation feature with a post-backup process is not suppported.
*When using with an RDX license
*This section is not applicable to ActiveImage Protector distributed in North America.
Instead of enabling Destination Isolation option, configure "RDX data cartridge eject setting" as shown below.
· Weekly:The cartridge is ejected for the last incremental backup task scheduled on the specified day(s) of a week.
· Daily:The cartridge is ejected at a specified time after full or incremental backup. When the time comes to eject the cartridge during backup process, ejection of the cartridge is suspended.
· When backup task completes:The cartridge is ejected after a full or incremental backup completes.
· Not Eject: Do no eject the cartridge.
Backup Options
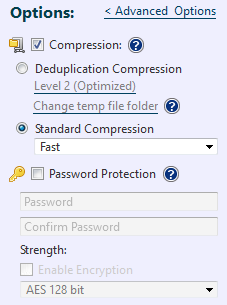
The backup options include features to improve [Compression], set [Password Protection], and to designate a level of [Encryption] for the backup image file. Select a post-backup operation (shutdown or reboot).
Backup Options and Advanced Options
-
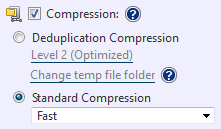
Compression: Enabling compression reduces storage requirements by further compacting the backup image file. Begin by checking the [Compression] box, then selecting the desired type of compression.
-
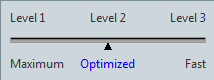
Deduplication Compression: Select one of the three levels of deduplication available.
[Level 1] - Deduplication is performed at the highest level. This level of compression may increase the overall backup processing time but achieves the most tightly compressed image file.
[Level 2] - This preset level provides the best balance between process time and compression performance. (This is the default setting).
[Level 3] - The image file will be generated at a lower compression rate and deduplication requires less backup processing time.
Use the curser to drag the slide switch to the desired level of deduplication compression.
-
Temporary File Folder: Set the location for deduplication to process temporary files.
* The maximum size of the temporary file folder will be 1% of the used space of backup source. The higher the deduplication level, the more increase the size of the temporary file.
-
Standard Compression: The dropdown menu provides two levels of standard compression.
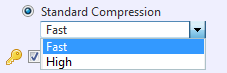
[Fast] - Backup processing time and storage requirements are at an optimum.
[High] - The backup task will place a higher demand on system resource usage and an increase in processing time but the result is a smaller backup image.
-
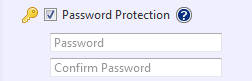
Password Protection: Password protect the backup image file by assigning a unique password. This ensures that password input is required for mounting, exploring, or restoring any of the contents of the image file.
Enable [Password Protection] by first checking the box, then setting the password.
-
Enable Encryption: Enabling the encryption for the backup image file ensures that the backup file cannot be compromised. There are three levels of encryption to choose from. RC5, AES 128 or AES 256 bit.
Enable Encryption by first checking the box then use the drop down menu to select an encryption method.
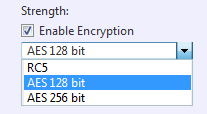
The three levels of encryption to choose from are as follows.
[RC5] - An early encryption standard with a variable block size, key size and number of rounds. Selecting RC5 encryption provides a faster encryption processing speed.
[AES 128 bit] and [AES 256 bit] - A stronger encryption method than RC5 with a fixed block size and a key size of 128 or 256 bits.
Configure the advanced backup options or refer here to create a backup schedule.
Advanced Backup Options
Click [Advanced Options] to access the advanced backup options settings page.
[Advanced Backup Options] offer a number of customized settings that can be configured into the backup task by checking the box at each of the options. Backup file options include streamlining the backup process, generating an MD5 checksum file, and adjusting network throttling for the backup task traffic.
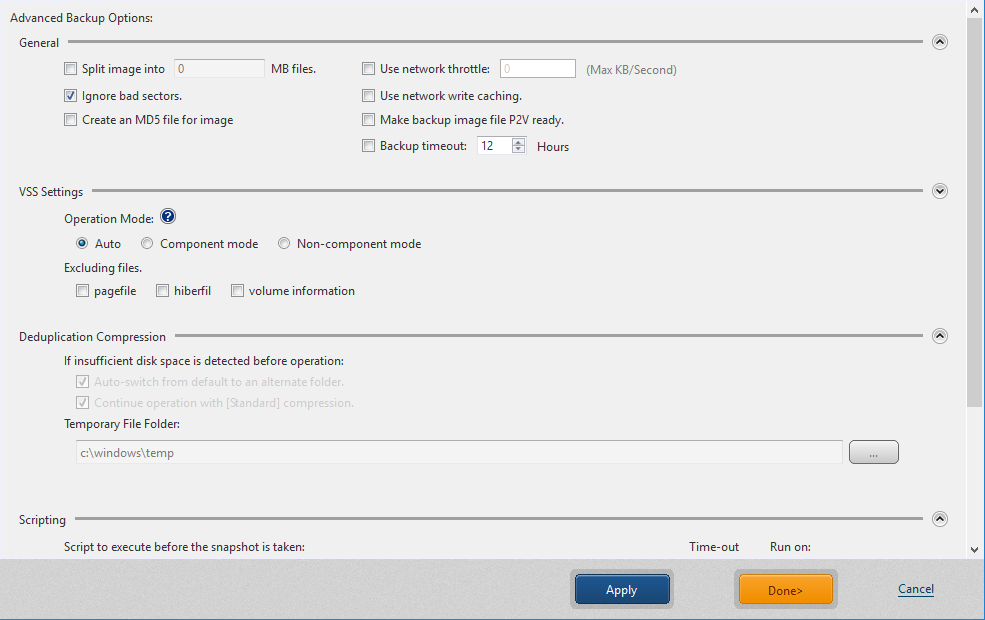
General
Split image into xx MB files - The backup image is split into multiple files of the specified size (MB)
Ignore bad sectors - By enabling Ignore Bad Sectors, the backup task will continue uninterrupted if encountering unreadable sectors.
Creates an MD5 check-sum for the image file - This can be used as a security measure to check if internal tampering of the image file has occurred.
Ignore inaccessbile volume - By enabling this option, the backup task will continue uninterrupted if encountering unaccessible volume.
Ex: When selecting backup source system volume and shared volumes in cluster environment on Server 2008 R2 and enabling this option, the backup task will continue uninterrupted even if a shared volume was moved to another node in the cluster.
* Desktop Edition does not support this option.
Use network throttle - If the destination drive is on a network share, use network throttle to define the maximum throughput in KB/second to reduce backup traffic over the network.
Use network write caching - When storing image files in network shared folder, cached data are used.
Make backup image file P2V ready - Performs the same process as required for [Virtualization] during backup but includes the installation of the driver required for virtualization (VMware ESXi/Microsoft Hyper-V), and changing the registry settings, etc.
Enable this option if intending to use the backup image file for the following purposes.
- Directly connect the image mounted by using [iSCSI Target Server] to a virtual machine and boot it up.
- Instead of using [Virtualization], restore the backup image directly to a virtual machine.
Backup time-out - Specify the time-out and the maximum time to wait for a backup task to complete the backup process.
VSS Settings
Edit the VSS settings for a backup task. Changing this setting in most cases is not necessary.

Operation Mode - Check in the check box for [Component Mode] to run VSS in component mode in backup process. Enabling VSS component mode runs the additional Verify data task (if supported) before execution of a backup task.
[Component Mode] - VSS component mode is enabled for every VSS writer.
[Non-component mode] - VSS component mode is disabled for every VSS writer.
Excluding Files - You can specify the items to exclude from backup process.
* If selecting (System) Volume Information, [Recovery Points] are excluded.
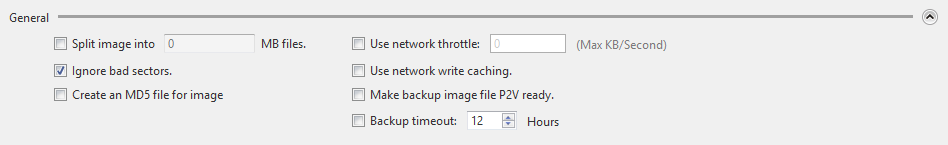
Deduplication Compression
Select the option to ensure that the backup task completes without interruption if insufficient disk space is detected in the temporary file folder before operation.
Auto-switch from default to an alternate folder - The temporary file folder used by deduplication will automatically switch over if insufficient disk space is detected.
Continue operation with [Standard] Compression - Will complete the backup task using the default Standard Compression.
Temporary File Folder - Specify the location for deduplication to process temporary files. The maximum size of the temporary file folder will be 1% of the used space of backup source or less. The higher the deduplication level, the larger the temporary file size will be.
Scripting
Scripts can be implemented to run before and or after snapshots are taken or after the backup image has been created. Use the dialog box below to execute scripts.
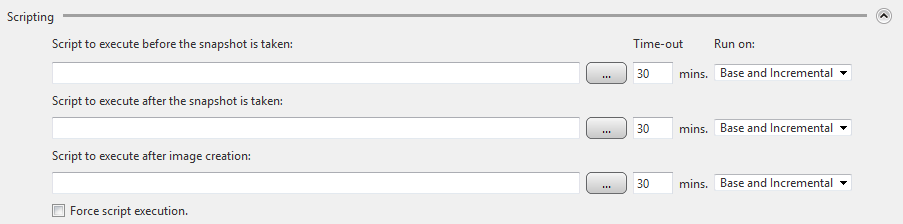
Enter the path and script to run or use the browse button  to select a script (the specified script files must not require user interaction) to be executed before/after the backup task.
to select a script (the specified script files must not require user interaction) to be executed before/after the backup task.
An example would be to execute a script that places a database into a paused state before a snapshot is taken.
Script to execute before the snapshot is taken - Specify a script or batch file to run before the snapshot is taken.
Script to execute after the snapshot is taken - Specify a script or batch file to run after the snapshot is taken.
Script to execute after image creation - Specify a script or batch file to run after the backup image has been created.
Force script execution - Checking this box ensures that all specified script or batch files will be executed even if an error occurs during the backup operation.
Cluster Node
Scripts configure the settings to back up Cluster Shared Volume (CSV) on which a virtual machine is running in Windows Server Failover Clustering (WSFC). Please enter the credentials for the domain administrator in Domain Admins group to obtain the information from the respective virtual machine's owner node.
To confirm the network connection, click [Test Connection].
Click [Done] to complete the destination setting.
Click [Next] to create a backup schedule
Click here to Step 3: Create Backup Schedule